System at a glance
A lightweight attendance system that uses face embeddings stored in Google Sheets. Lecturers generate time-bound, WiFi-restricted verification links; students verify their faces and have attendance automatically marked on the lecturer sheet.
1. Architecture & Flow
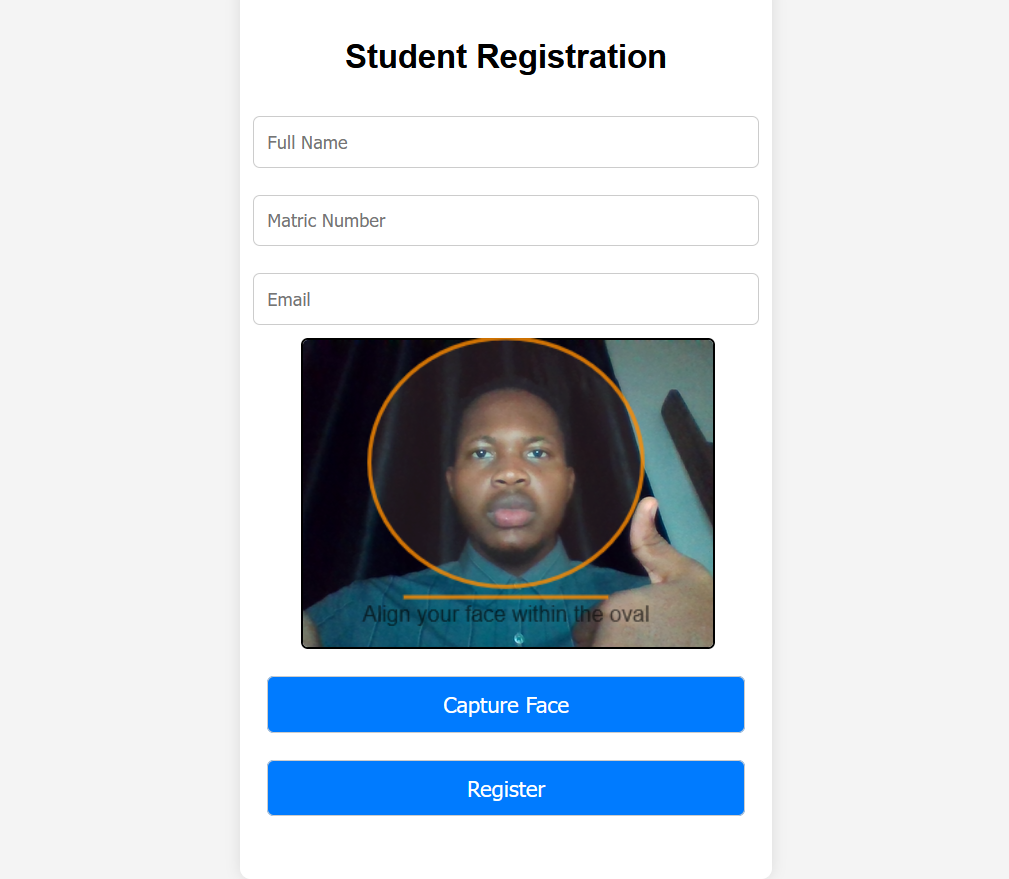
Student Registration
- Frontend form collects Name, Matric No, Email, Face Embedding (128-d)
- Saves complete record to Main Google Sheet (Registration Sheet).
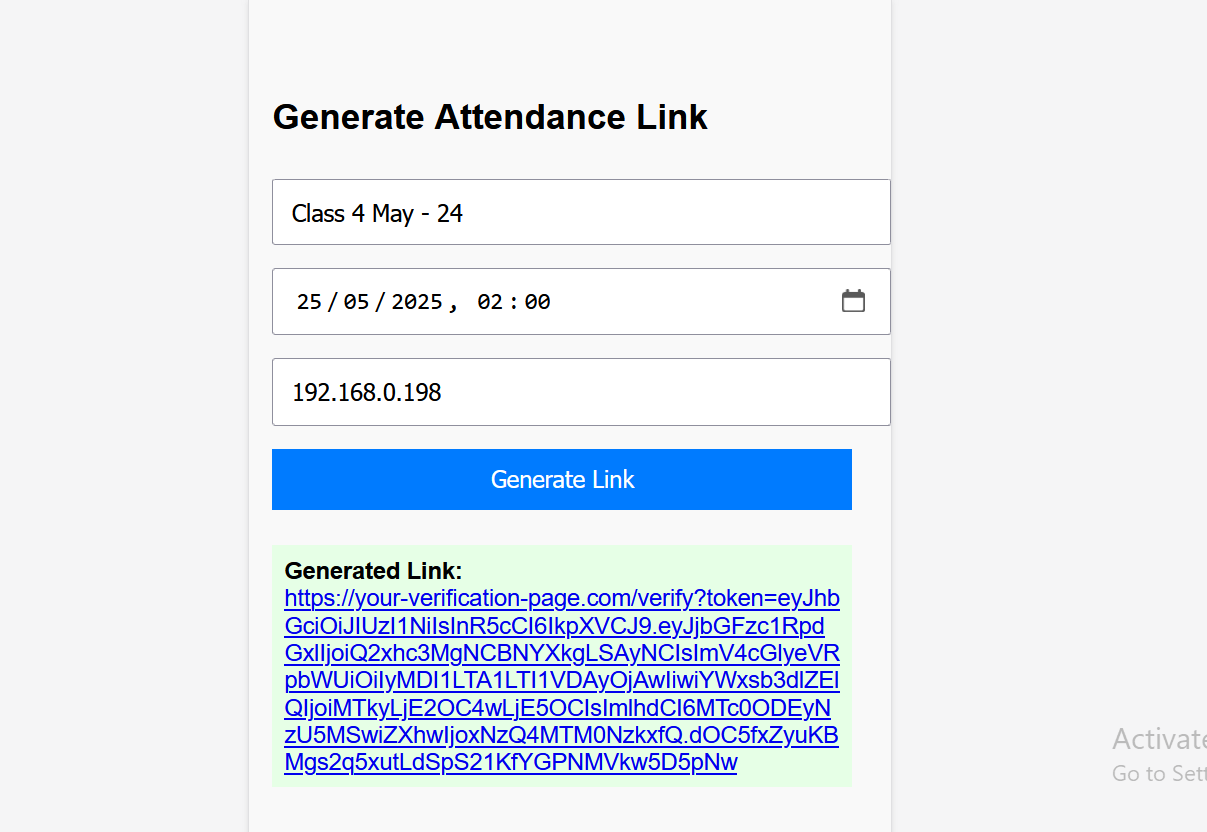
Lecturer Portal
- Generate class-specific verification links with encrypted tokens.
- Tokens include: class date/column name, expiry timestamp, WiFi/IP constraints.
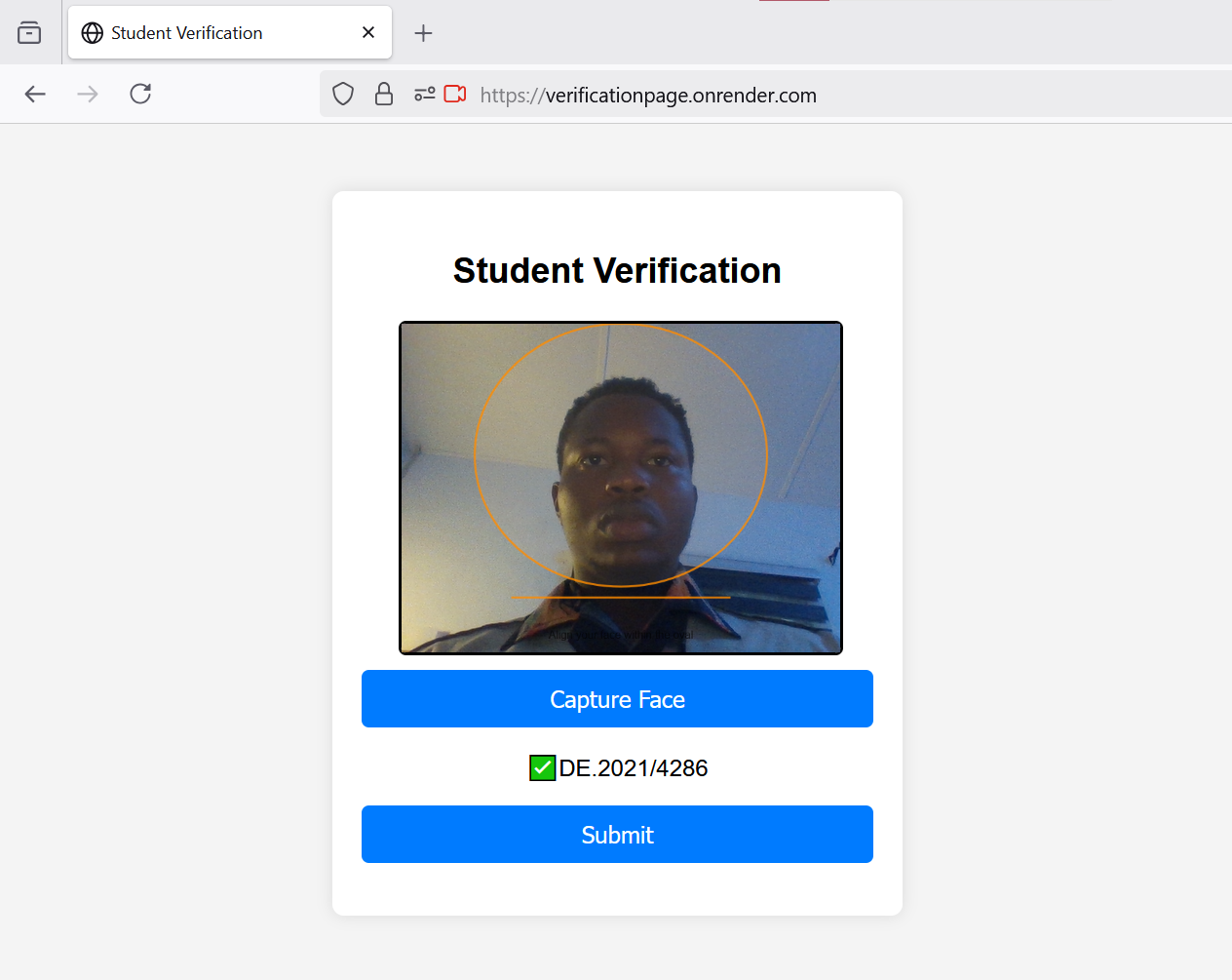
Verification Service
- Verifies token conditions (time, WiFi/IP).
- Runs face matching against Registration Sheet; if match found, marks "Present" on Lecturer Sheet for the appropriate class column.
Quick flow diagram
🧑🎓
Student registers → embedding saved
➡️
👩🏫
Lecturer generates tokenized link
➡️
🔐
Verification page checks token, WiFi & time
➡️
✅
Match → Mark & update Lecturer Sheet
2. Data schema (Google Sheets)
Registration Sheet (Main)
| Name | Matric No | Embedding | |
|---|---|---|---|
| Ada | CS/1001 | ada@uni.edu | 128-d array |
Lecturer Sheet (Attendance)
| Name | Matric No | Class 1 (Apr 25) | Class 2 (May 2) |
|---|---|---|---|
| Ada | CS/1001 | Present |
3. Token example & verification logic
Tokens are short opaque strings produced by the server. They include encrypted data such as the class column label, expiry timestamp, and allowed WiFi/ IP pattern.
Example (pseudo)
/verify?token=ENCRYPTED_DATA ENCRYPTED_DATA -> { "classColumn": "Class 4 (May 9)", "expiry": 1683655200, "wifi": "DEPT-LAB-SSID", "allowedIps": ["10.0.1.0/24"] }
Verification check flow (server)
- Decode and decrypt token.
- Ensure current time < expiry.
- Check student's client WiFi name or IP address matches constraints.
- If allowed, run face matching against Registration Sheet.
- If match found, retrieve matricNo and update Lecturer Sheet at the target column with "Present" (idempotent write).
Idempotency & safety
- Do not overwrite an existing cell unless desired; only set "Present" if cell is blank.
- Log successful writes with timestamp and verified matricNo.
- Rate-limit verification requests to avoid abuse.
4. Implementation notes
- Frontend: simple React or vanilla JS page that captures face, computes embedding (face-api.js), and POSTs to the verification endpoint.
- Server: Node.js/Express that issues encrypted tokens, validates token + constraints, and updates Google Sheets via the Google Sheets API using a service account.
- Security: use strong encryption for tokens (AES or RSA), store secrets in environment variables, verify token timestamps carefully.
- Face matching: cosine similarity threshold (e.g., 0.45-0.6 depending on model). Pre-normalize embeddings before comparing.
- Deployment: host verification page on Render, Vercel, or similar; server can be a separate Render service. Keep CORS and CSP tight.